HTTPS has numerous benefits for your website. Learn why you should use it immediately to gain visitor trust and possibly a performance boost.

HTTPS stands for HyperText Transfer Protocol Secure, it’s also referred to as SSL (Secure Sockets Layer). It allows browser sessions with a website to occur over an encrypted communication channel. If you like people visiting your website, it’s important to ensure you’re running HTTPS. Sounds dramatic, doesn’t it? The Chrome browser already labels sites without HTTPS as “Not secure”, which leaves it up to your customers to interpret. I wouldn’t be surprised if someday, all browsers do this.
- What it looks like
- The superficial reasons to switch
- The technical reasons to switch
- Where to get it
- How to install it
- Stop using http://
- Keep up-to-date
What it looks like
It’s easy to see if a site is communicating over this protocol, just look for a green lock (or grey), next to the website address starting with https://.
Different browsers display different things, here is a sample of some scenarios:
Secure and proper configuration:
![]()
![]()
![]()
This certificate has “Trust” – see below in the “Where to get it” section.

Android/Firefox

iOS/Safari
Secure with some insecure elements:
![]()
Firefox
![]()
Chrome doesn’t mess around, having insecure elements means insecure.
Insecure:
![]()
Firefox
![]()
Chrome

Android/Firefox

Android/Chrome
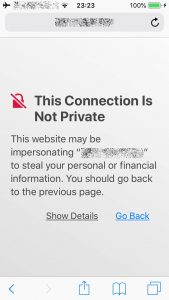
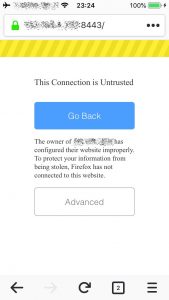
These last two are slightly different. They’re on iOS on Safari, and Firefox. The connection really is secured, but the warning happens because the SSL certificate mismatches the specified URL. It’s more of a trust issue because the certificate claims it’s one site, while the visited URL is different.
The superficial reasons to switch
These reasons don’t do anything from a customer standpoint, but they really make you look good!
- Green = Good. That address bar just looks more trustworthy in green!
- Search Engine Rankings – Some search engines (Google) will rank your site higher simply because you have HTTPS enabled. Our article – Technical SEO covers this, along with other Technical SEO optimizations.
The technical reasons to switch
- HTTPS ensures an encrypted communications channel between browsers and websites. This prevents the ability of others to intercept everything you do on the browser. Even if you have nothing to hide, the ability to intercept your browsing sessions can lead to hacking, or identity theft. Using non-HTTPS sites on open Wifi access points leaves you vulnerable.
This screenshot shows a tool called tcpdump being used to view HTTP requests. Without encryption, you can see the headers, and HTML from the site. This is only a redirect page, so it’s nothing special, but you can definitely read emails or other sensitive information using these tools.
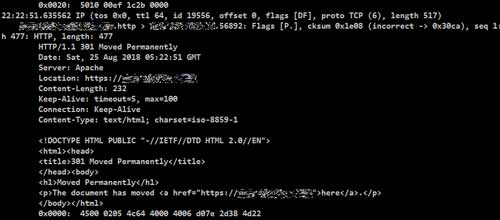
What does it look like with encryption? Gibberish. - Allows the use of HTTP/2 which speeds page load time.
- Less likely for mass surveillance to track you, if you care.
Where to get it
All methods require some level of technical knowledge. If you have an IT person, reach out to them. AppLite can also help with this – [email protected]
HTTPS is just HTTP transported over Secure Sockets Layer (SSL) or Transport Layer Security (TLS). TLS is currently the accepted protocol, while SSL is deprecated, but most of the internet continues to call the encryption certificates “SSL Certificates”. Here are some methods to get started with HTTPS:
- CloudFlare – This is the easiest way. CloudFlare would act as the middleman between customers and your server(s). This sounds like it would incur a performance penalty by introducing an intermediary hop, but CloudFlare is known for it’s optimized and fast network. There’s few real world scenarios where CloudFlare actually slows down a site. You also get security, CDN, asset optimization, and more… for free!
You only need access to your domain name’s provider to change DNS settings.
https://www.cloudflare.com/
Note: CloudFlare’s solution fully encrypts communications between the user and Cloudflare. The communication between CloudFlare and your server may not be encrypted unless you manually install certificates as discussed below. See https://www.cloudflare.com/ssl/ for more detailed information. - Server-Side (Free)
- Let’s Encrypt: Free certificates that must be renewed every 90 days. Set up a cronjob to automate the renewal task. Recently, Let’s Encrypt began offering wildcard certificates so support all subdomains within a primary domain.
https://letsencrypt.org/ - Comodo: Also free, and requires renewal every 90 days.
https://ssl.comodo.com/free-ssl-certificate.php
- Let’s Encrypt: Free certificates that must be renewed every 90 days. Set up a cronjob to automate the renewal task. Recently, Let’s Encrypt began offering wildcard certificates so support all subdomains within a primary domain.
- Server-Side (Paid) – Why pay for a certificate? Technically, there is NO difference between the encryption offered by free or paid certificates. Your considerations here are: Vendor requirements – some require that your site is protected by a paid certificate from a vendor that insures your site from certificate problems, and the appearance of “trust” – The certificate provider verifies an applicant company’s details; in addition to a display in the address bar showing your company name and displaying company information.
Trust! [Trust Image]- Comodo: https://ssl.comodo.com/free-ssl-certificate.php
- GoDaddy: https://www.godaddy.com/web-security/ssl-certificate
- Network Solutions: https://www.networksolutions.com/SSL-certificates/index.jsp
- DigiCert: https://www.digicert.com/ssl-certificate/
- There are so many more, I can’t list all of them!
Don’t pay for a Certificate unless there’s a clear need.
How to install it
All of these providers have instructions for installing these certificates. There’s so many operating system and web server variation that this article won’t cover it. Here are some starting points from the various providers:
CloudFlare: https://support.cloudflare.com/hc/en-us/articles/218408028-How-to-install-an-Origin-CA-Certificate-Other-
Let’s Encrypt: https://letsencrypt.org/getting-started/
Comodo: https://support.comodo.com/index.php?/comodo/Knowledgebase/List/Index/37
GoDaddy: https://www.godaddy.com/help/install-ssl-certificates-16623
Network Solutions: http://www.networksolutions.com/support/installing-ssl-certificate-topics/
DigiCert: https://www.digicert.com/ssl-certificate-installation.htm
Note: All instructions from these providers are mostly the same content; they tailor to their method of certificate naming.
Stop using http://
There is no benefit to using regular old HTTP. Any requests to your HTTP site should automatically redirect to HTTPS, and all references to the old HTTP should be removed.
- Website References: If you haven’t done so already, replace all references to your site’s URLs from “http://” to “//” (protocol-less). Better yet, remove any references to the protocol and domain name, because browsers already know what domain they’re on. For example: If your site is “example.com” and your home page references the image “http://example.com/images/helloworld.png”, change it to: “/images/helloworld.png”. It will continue to work on any protocol. You can do this at any time, even before switching to HTTPS.
- Automatic redirection: All requests to the http:// version of your site should automatically redirect to https://. This can be done in all web server software. Search engine ranking is not affected on any good search engine. The warnings here – Changing Domain Names While Keeping Search Rankings – Do not apply, but it’s a good idea to update Search Engine Consoles as described in the article.
- Update e-mail signatures, or links you control. It’s not a big deal, but the auto-redirect from http:// to https:// does take an additional round trip request from client browser to web server.
Keep Up-to-Date
Security only lasts so long. At the moment, these technologies are secure, but secure things will become insecure given enough time. If you want peace of mind, It’s important to have your technical resources update software to address the latest vulnerabilities.

PS: If you ever want to have a sleep-less night, check out the database of vulnerabilities at US-CERT.
